ipTables Tutorial
ipTables is definitely confusing to begin with, but for an unmanaged VPS server it is a completely necessary part. This
ipTables tutorial will not necessarily be as in-depth as some which are available, simply as I don't know as much! However, I will link to any
ipTables tutorial which I have used or I think is worthy of a read.
UPDATE: Automatically update your iptables with Spamhaus Drop List of Spam IPs
Skip to it hereipTables, Tables, Chains and Rules
There a different parts of ipTables which make up the structure, but it is only that; a structure. It isn't particularly hard to underdtand the structure, but it will make a big difference as to understanding ipTables.
Structure - you can have multiple tables, and with those tables, multiple chains, and within those chains, multiple rules.
Table:
Chain 1
Firewall Rule 1
Firewall Rule 2
Chain 2
Firewall Rule 1
Firewall Rule 2
Firewall Rule 3
So, a collection firewall rules make up a chain, and a collection of chains make up a table.
There are a number of pre-configured tables when you install ipTables, and they are "Filter Table", "NAT Table", "Mangle Table", and "Raw table".
"Filter" is the default table which is used if you do not add your own table, and This is the table I will be altering.
Filter contains the following chains:
INPUT - Incoming
OUTPUT - Outgoing
FORWARD - For sending data to other computers on the same server
ipTables rules work in a similar way to conditional statements in languages such as PHP. They contain a condition which is either matched or not matched and a consequent ("target") if the condition is met. The consequent can either be rules or the execution of special values
ipTables use the structure:
[rule number] [target] [protocol] [option] [source] [destination]
The values which can be specified in "Target" are:
[Accept] The firewall let the data through
[Drop] The firewall ignore the data
[Queue] The firewall the data is made available to "userland" applications
[Return] The next set of rule in the chain are ignored, and instead, control is returned to the "calling" chain.
Before I add any rules, I first need to install ipTables using the command "sudo apt-get install iptables". For good practice, I will export the default ruleset with the command "sudo iptables-save > /home/randoof/iptables.default.rules
Next, I need to create my ruleset for the "Filter" table by first creating a file "nano /home/randoof/iptables.rules.new" and then using the following rules (which you can find
here)
*filter
# Allows all loopback (lo0) traffic and drop all traffic to 127/8 that doesn't use lo0
-A INPUT -i lo -j ACCEPT
-A INPUT ! -i lo -d 127.0.0.0/8 -j REJECT
# Accepts all established inbound connections
-A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# Allows all outbound traffic
# You could modify this to only allow certain traffic
-A OUTPUT -j ACCEPT
# Allows HTTP and HTTPS connections from anywhere (the normal ports for websites)
-A INPUT -p tcp --dport 80 -j ACCEPT
-A INPUT -p tcp --dport 443 -j ACCEPT
# Allows SSH connections for script kiddies
# THE -dport NUMBER IS THE SAME ONE YOU SET UP IN THE SSHD_CONFIG FILE
-A INPUT -p tcp -m state --state NEW --dport 30000 -j ACCEPT
# Now you should read up on iptables rules and consider whether ssh access
# for everyone is really desired. Most likely you will only allow access from certain IPs.
# Allow ping
-A INPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT
# log iptables denied calls (access via 'dmesg' command)
-A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables denied: " --log-level 7
# Reject all other inbound - default deny unless explicitly allowed policy:
-A INPUT -j REJECT
-A FORWARD -j REJECT
COMMIT
Once I have saved the file, I then need to import it into iptables with the command "sudo iptables-restore < iptables.new.rules"
The next thing I need to do is ensure that my ruleset is restored to iptables at every system reboot. I can do this by editing the "rc.local" file located in the "etc" directory, which executes any listed commands when the system reboots. So "sudo nano /etc/rc.local". Currently, my rc.local file has no commands, so I just need to add the iptables-restore command so it will be run automatically.
The iptables binaries are stored in the /sbin directory, so it's important to include that in the restore command, so: "/sbin/iptables-restore < /home/randoof/iptables.new.rules".
Make sure to change the port number to the one you configured in the "sshd_config" file.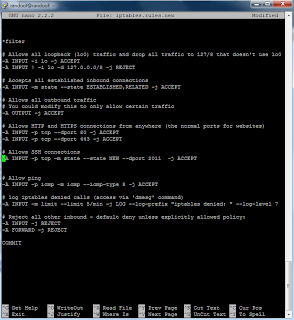
Once that is complete, all I need to do is reboot restart ssh with the command "/etc/init.d/ssh restart" and then I will reboot the system - "reboot" - and log back in, then check my ipTables configurations have been loaded using the command "sudo iptables -L", which then lists all of my tables, chains and rules.
Automatically add Spamhaus Drop List to IPtablesWhether you have read the iptables tutorial above or not, one of the most helpful things it to be able to
block ips with iptables. You can do this manually by updating your iptables rules file with the following line:
-A INPUT -s 123.456.1.18 -j DROPAll you need to do is input the ip address you wish to block instead of 123.456.1.18
That's all well and good, but what if, rather than reactive, you wish to be proactive and
block ips with iptables automatically? Then you need to to automatically add Spamhaus drop list to iptables. That is possible with a little scripting. Below is a file which I have modified slightly in order for me to be able to automatically add Spamhaus drop list to iptables using cron
Let's check our current IPtables rules:
sudo iptables -L
Firstly, create a bash script
nano iptables_update.sh
and paste the following code:
#download the latest spamhaus ip drop list
wget http://www.spamhaus.org/drop/drop.lasso -O drop.lasso
if [ -n "$1" ]; then
DropList="$1"
else
DropList="./drop.lasso"
fi
cat "$DropList" \
| sed -e 's/;.*//' \
| grep -v '^ *$' \
| while read OneNetBlock ; do
/sbin/iptables -I INPUT -s "$OneNetBlock" -j DROP
/sbin/iptables -I OUTPUT -d "$OneNetBlock" -j DROP
/sbin/iptables -I FORWARD -s "$OneNetBlock" -j DROP
/sbin/iptables -I FORWARD -d "$OneNetBlock" -j DROP
done
Basically, this downloads the latest Spamhaus ip Droplist, and steps through the list, creating the rules for each ip address, automatically adding the ip address to the iptables filter.
Please note in order to automatically add the Spamhaus ip drop list to iptables, you first require wget to be installed (sudo apt-get install wget).
Now, if we check
sudo iptables -L
it will now list all of the Spamhaus ip drop list (albeit probably quite slowly, in which case you can cancel with CTRL+C)
Spamhaus requests that you do not download the drop list more than once an hour, and advises just once a day, which is what I do. I run the bash script automactically during a quiet time for my server using Crontab:
sudo crontab -e
and then adding the line:
#automatically add Spamhaus drop list to iptables at 3.45am
45 3 * * * /bin/bash /home/randoof/iptables_update.sh
This line will run the bash script as sudo (required to update iptables) at 3.45am every morning.
That's it for another entry, please remember to click an advert if I have helped you :)
As promised, here are some helpful links which I used as reference for what has definitey been the most complicated step in my unmanaged VPS ipTables Tutorial:
Ubuntu Forums
The Geek Stuff ipTables introduction - Extremely helpful.
Debian Wiki ipTables ruleset basic configuration

